ORing's proprietary Device Binding effectively binds the IP/MAC address of the device connected with the switch port. If the IP/MAC address of the connecting device does not match the switch port binding information, the device will be blocked for security. Additionally, the bound device also benefits from a collection of active network traffic protection and maintenance tools :
- Alive Check
- Stream Check
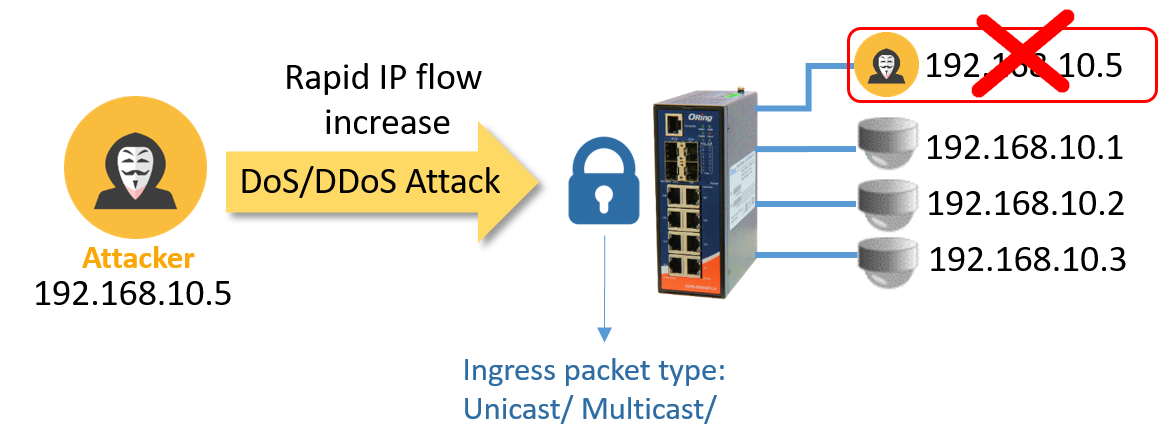
- DoS/DDoS Auto Prevention
The Alive Check monitors the real-time status of a connected PD (powered device, e.g. PoE IP camera) bound to the port. Alive-checking packets are sent to the PD to assure the device is in working state. If the connected PD fails to response, ORing’s managed PoE switch can reactivate the connected PDs to assure the reliability of the network.

The Stream Check monitors the continuity of real-time data flow from the bound device. If suddenly there is a big drop of the data flow, a warning log event of such unusual phenomenon will be quickly dispatched. In conjunction with Open-Vision, ORing’s powerful network management software, the bound device failing the streaming check will also be visually indicated on the network topology in Open-Vision’s Topology View, giving the network administrator a chance to properly respond to the situation.